
For many years, Cyber Risk Management was interpreted as a simple control exercise, limited to specific and infrequent moments in time. The underlying idea was to bring order to complex environments through activities aimed at understanding what existed, assessing risk at predefined intervals, and demonstrating that security measures were in place and operational.
This approach proved coherent and effective only in relatively stable contexts, where infrastructures evolved slowly, perimeters were easier to define, and application dependencies were simpler to reconstruct.
In such scenarios, an accurate snapshot of the IT environment could remain representative over time, and a static risk assessment could provide sufficiently reliable guidance even for sensitive decisions. This model played an important role by introducing discipline, a shared language, and the first structured mechanisms for risk governance.
Modern infrastructures have reached an unprecedented level of complexity and dynamism. Cloud adoption has made change continuous, hybrid architectures have multiplied interconnections, and the digital ecosystem has expanded well beyond traditional IT boundaries. A growing share of business processes now depends on systems that operate entirely outside the organization, yet directly affect daily operational continuity.
In this context, risk no longer emerges only as a consequence of a deliberate attack. It can change every time the organization modifies any aspect of its operational setup. Technical choices that are perfectly legitimate and often necessary can alter exposure without generating clear or immediate warning signals. Risk may therefore originate from internal changes, not exclusively from external adversaries.
An often underestimated factor further amplifies this issue: time. Traditional risk management processes operate on cycles measured in weeks or months, while perimeter conditions can shift within hours, sometimes as a result of seemingly minor configuration changes.
As a result, the gap between what is believed to be under control and what actually exists widens exponentially, making the use of automated tools unavoidable in order to overcome the intrinsic limits of manual intervention.
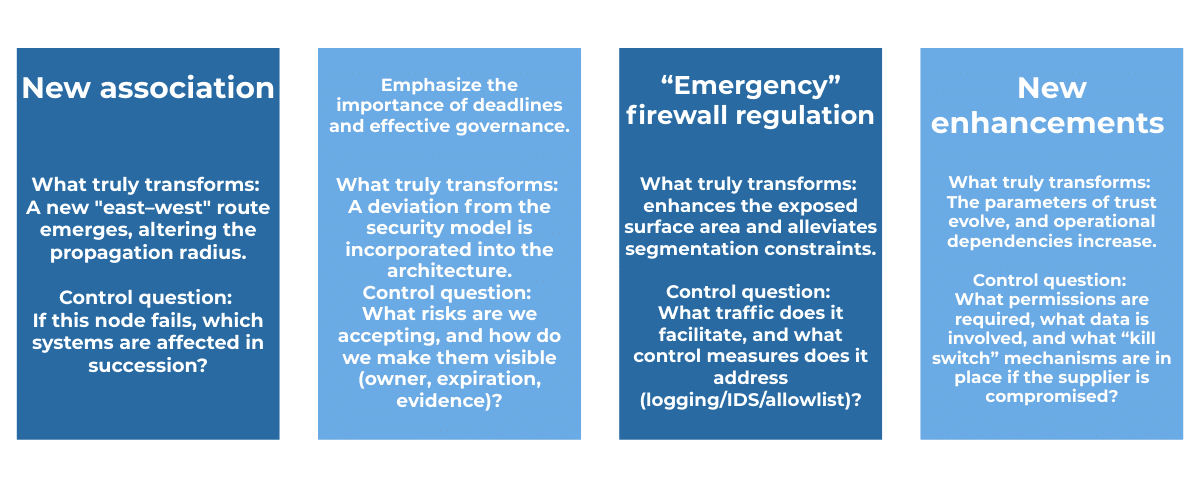
One of the most evident limitations of traditional models lies in how risk is represented: as a localized and controllable issue, manageable through isolated interventions.
This interpretation is reassuring because it supports a linear cause-and-effect logic and creates the illusion that risk is “resolved” once an action is completed. In practice, however, it oversimplifies a far more articulated reality.
In real organizational environments, risk rarely remains confined to the point where it is identified. Instead, it propagates along relationships between assets, applications, and processes, amplifying its impact depending on the paths available.
When risk distributes itself in this way, focusing on individual elements becomes ineffective. What is required is an understanding of the behavior of the entire system, in order to assess whether exposure remains manageable or is likely to evolve into material impact.
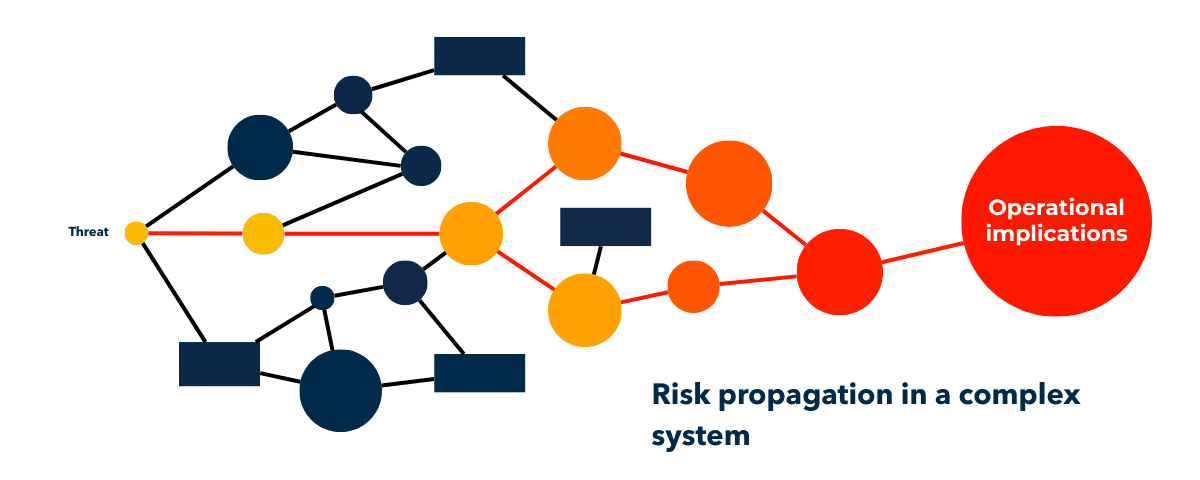
These considerations make it clear that awareness lies at the core of the new Cyber Risk Management paradigm.
Awareness emerges when attention shifts from objects to paths, from assets to processes, and from isolated conditions to operational dependencies. This transition often creates friction, because understanding what is truly at stake exposes gray areas and decisions that can no longer be postponed.
Risk has therefore become a foundational element of decision-making and must be readable by those responsible for strategic choices, rather than remaining confined to a purely technical domain.
Today, decision-makers must be able to interpret risk in terms of time, cost, and accountability, not just technical severity.
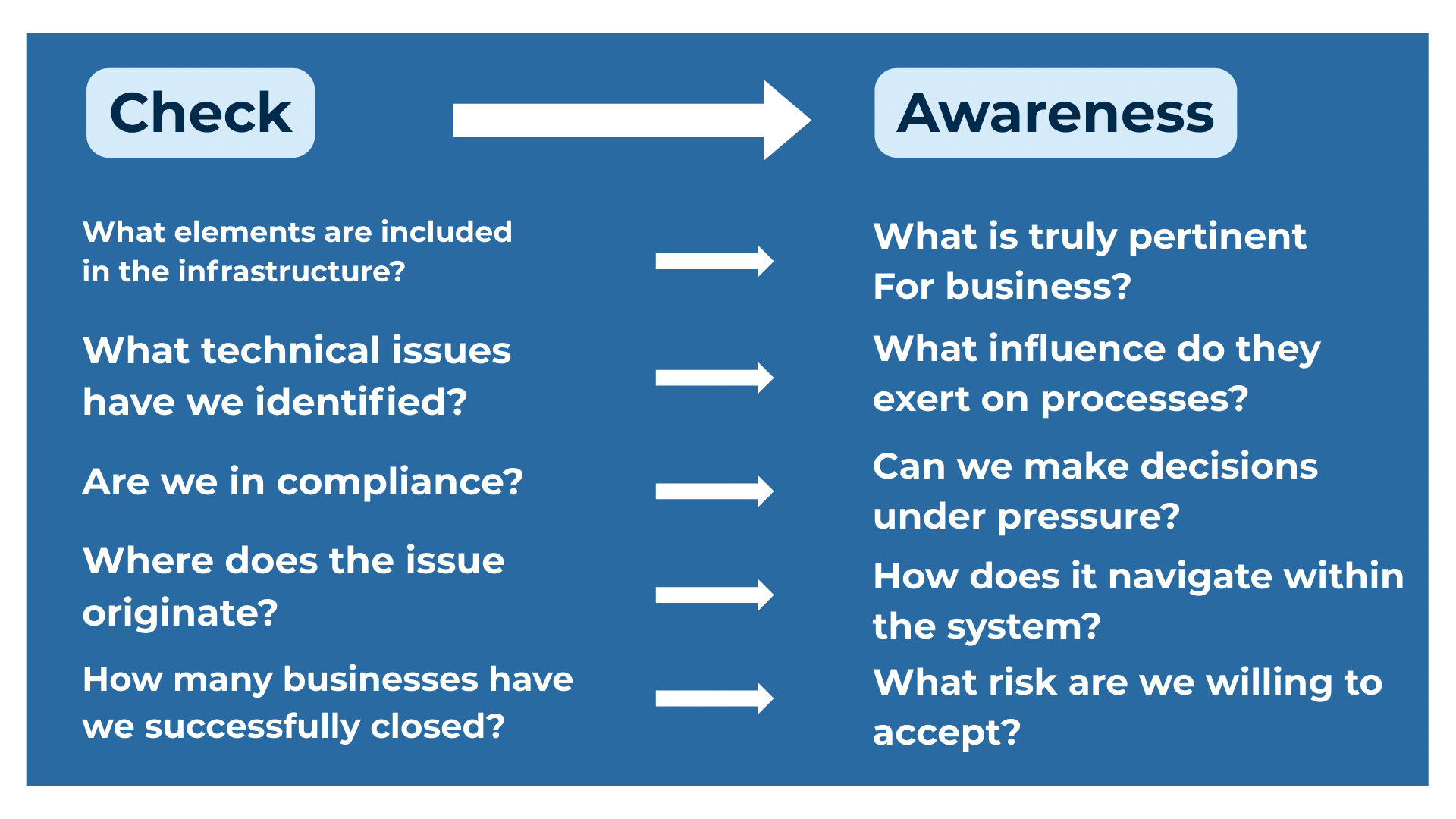
This evolution requires a change in language before a change in tools. For a long time, security teams communicated through indicators suited for technical operations but poorly aligned with organizational decision-making.
Executives are not looking for vulnerability lists or patching metrics, but for a clear understanding of the exposure being assumed and the consequences of ongoing choices.
Within this context, the role of the CISO evolves. It becomes an interpretative role, tasked with holding together technical accuracy and strategic readability. Information must be robust enough to support real decisions, even when those decisions involve trade-offs or the conscious acceptance of risk.
The true maturity of Cyber Risk Management is reflected in the ability to maintain coherence over time, even as scenarios change and priorities are redefined.
The transformation described above shows that Cyber Risk Management can no longer rely on static snapshots or periodic control exercises. When risk evolves alongside the organization, continuous visibility of the digital ecosystem becomes essential.
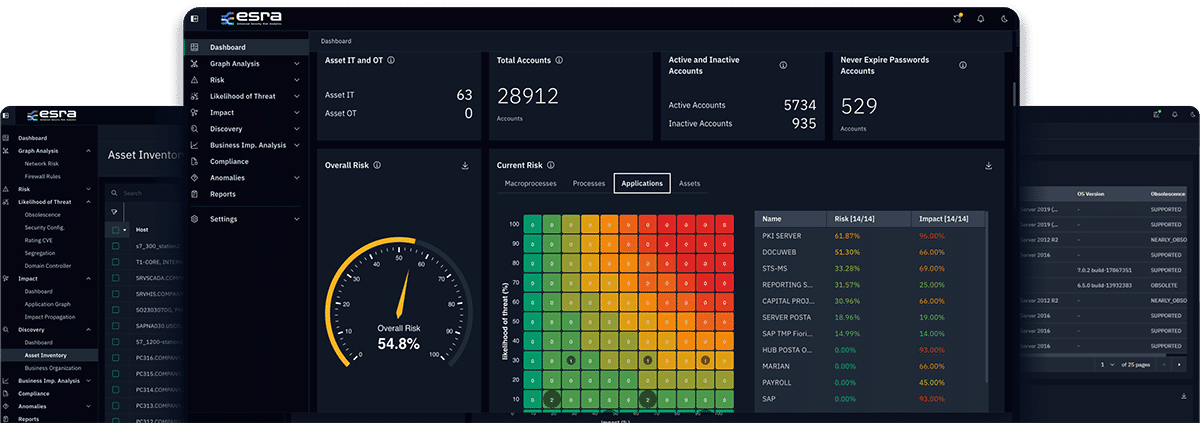
ai.esra addresses this need by enabling organizations to understand risk over time, correlating infrastructure, applications, and processes, and making the impact of operational decisions visible before they materialize.
ai.esra SpA – strada del Lionetto 6 Torino, Italy, 10146
Tel +39 011 234 4611
CAP. SOC. € 50.000,00 i.v. – REA TO1339590 CF e PI 13107650015
“This website is committed to ensuring digital accessibility in accordance with European regulations (EAA). To report accessibility issues, please write to: ai.esra@ai-esra.com”
ai.esra SpA – strada del Lionetto 6 Torino, Italy, 10146
Tel +39 011 234 4611
CAP. SOC. € 50.000,00 i.v. – REA TO1339590
CF e PI 13107650015
© 2024 Esra – All Rights Reserved